
2014 was wrought with headlines concerning the ever-increasing threat of malware. Massive data breaches the world over brought businesses to a standstill time and time again. Indeed, a study by Osterman Research Inc. which surveyed 157 companies found that 74% of organizations have had malware infiltrate their corporate network through web surfing over the past 12 months.
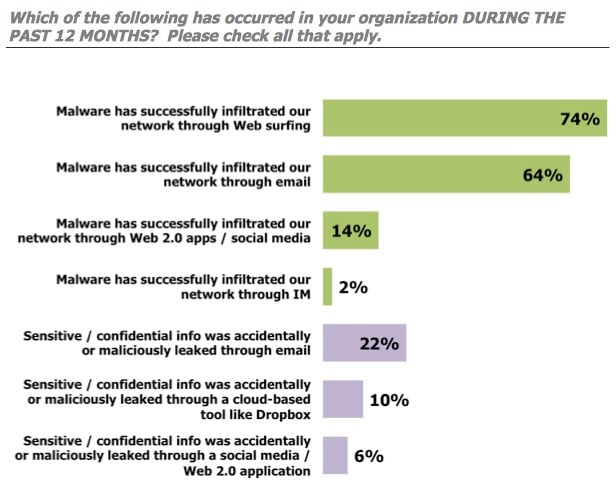
Web, email and social media are all targets for malware, and if your business is using them (and almost undoubtedly IT will be using all three) then without serious anti-malware protection moving forward, you are leaving yourself and your business vulnerable to a whole host of online threats that are becoming increasingly sophisticated as each new year ticks by.
Malware can be used for any number of devastating functions. From capturing sensitive information to establishing a controlling foothold within an organization’s network; malware is serious, and unfortunately it’s everywhere. And IT gets worse. What is quite often the case is that, in these technology-advanced times, the malware that tries to infiltrate business systems is custom designed in order that IT may evade traditional detection techniques. Signature-based methods that have long been the final frontier of malware threats these days simply do not have the intelligence to withstand today’s more sophisticated malware attacks.
With this in mind, security and IT professionals must consider using anti-malware services and technology that utilise a conditions and behavioural-based approach to identify potential malware on in-house networks and systems in real time.
Of course, firstly detecting and then subsequently deflecting malware attacks is the primary task of protecting a business, but there are more things to consider. One of the main objectives of the cybercriminal is remain anonymous for as long as possible so that they may continue to siphon off as much confidential intelligence as computably possible, and so, defenders of such information must consider the use of further technological tactics as part of their managed service to both prevent a compromise in the first instance, as well as signal that a breach is underway.
So, below we’ve put together a round up of some of the best additional technologies services that every business should be using to make sure that they are deploying the very best anti-malware protection available.
Web Application Firewall
Phishing links and email attachments are often the channels taken through which malware enters a system. However, attackers also like to use the web application layer to launch their malware attacks. As such, web application firewalls (WAFs) should be installed to provide the shield that is required to help close off this channel.
Network Access Control
Any unmanaged devices attempting to connect to a network should always be vetted. When done properly, alerts can be sent off to ensure that any contaminated endpoints do not end up spreading malware throughout a network.
Ethical Hacking
Ethical hacking is a security testing technique, which evaluates a network’s and application’s vulnerabilities and capabilities to withstand an attack. These tests should always be carried out by professionals and ideally as part of a managed services package. The identification of potential vulnerabilities that could enable malware to enter an environment is an essential part of all anti-malware initiatives.
Security Information and Event Management (SIEM)
SIEM is a threat management technology that comes into its own should hackers ever actually start to mount an attack – especially when they are either at the stage of conducting reconnaissance or attempting to move within a network towards more high-valued targets. During these stages, cybercriminals often try and use tools to try and steal poorly protected credentials and elevate their privileges and access within a system. Using SIEM means that you will have increased network visibility and monitoring capabilities, and you will be enabled to collect, correlate and analyse events that may signal an unusual activity.
Data Loss Prevention
This is absolutely essential. No matter how good your anti-malware efforts are, there will still be occasions when attackers will make IT through your security and get greasy paws on what they want. In this instance, you will need data loss prevention to help you firstly identify what has been compromised, and then put a halt to any sensitive information slipping out of the back door.
Database Scanning
The ultimate goal of most hackers is to land on the repositories that house an organization’s database. IT is imperative, therefore, that regular scanning of that database be carried out to uncover any weaknesses. Missing patches, for instance, configuration errors and easily crackable passwords must all be identified and dealt with promptly.
An organisation must always be prepared for a malware attack that could come from anywhere at any time. IT is an ongoing challenge for businesses of all sizes, and one that is most effectively controlled with managed services. Companies can better protect themselves if they build their anti-malware approach with web security gateways as their focus, and from there complementing IT with high-defence technologies such as those we have outlined above.
Contact us at V&C Solutions to find out how we can bolster your anti-malware arsenal for 2015.




